In the ever-evolving landscape of cyber threats, a new and alarming development has emerged with the discovery of an enhanced variant of the Vo1d botnet. This sophisticated threat has infected approximately 1.6 million Android TV devices
Continue ReadingMonth: February 2025
Your MFA Is No Match for Sneaky2FA
In early February 2025, the eSentire Threat Response Unit detected a sophisticated phishing attack associated with Sneaky2FA, an Adversary-in-the-Middle Phishing-as-a-Service kit designed to bypass two-factor authentication (MFA). This threat report delves into the details of this
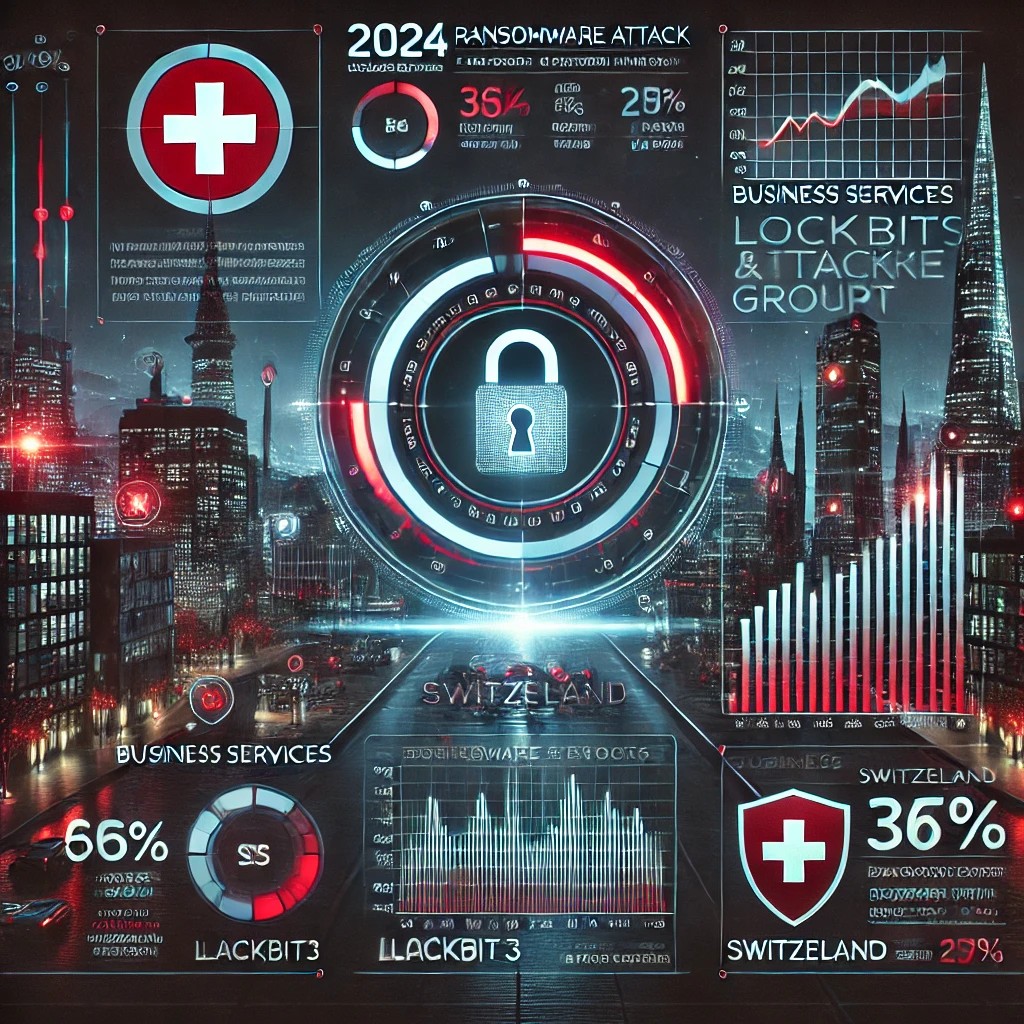
Continue ReadingThe Rise of Ransomware in 2024: Swiss Edition
The year 2024 has seen a significant rise in ransomware attacks targeting organizations across various sectors. This report provides an in-depth analysis of the ransomware incidents reported throughout the year, highlighting key metrics and analytics to
Continue ReadingNjrat Campaign Using Microsoft Dev Tunnels – SANS Internet Storm Center
In the ever-evolving landscape of cyber threats, a new and sophisticated strain of malware has emerged, leveraging Microsoft's dev tunnels service to connect to its command-and-control (C2) servers. This campaign, detailed in a recent threat report
Continue ReadingVulnerability Landscape Analysis Q4 2024 | Securelist
Threat Overview Kaspersky's Vulnerability Landscape Analysis for Q4 2024 has been published by CyberHunter_NL, highlighting the most common software vulnerabilities and their exploitation methods. The report is compiled by Alexander Kolesnikov from the University of California,
Continue ReadingTech Note – Malicious browser extensions impacting at least 3.2 million users – GitLab Security Tech Notes
In a recent threat report published by CyberHunter_NL on February 25, 2025, a significant cyber threat has been identified involving malicious Chrome extensions. This report highlights the discovery of at least 16 malicious browser extensions that
Continue ReadingUSB Worms: Still Wriggling Onto Under-Protected Computers After All These Years
Threat Overview Report Summary: ThreatDown has published a report detailing the resurgence of USB worms, once thought obsolete but now actively targeting under-protected systems via removable drives. The Jenxcus family is particularly prominent, exploiting weak endpoint
Continue ReadingConfluence Exploit Leads to LockBit Ransomware
Threat Report: Confluence Exploit Leads to LockBit Ransomware\n\nOn February 24, 2025, AlienVault published a threat report detailing an intrusion that began with the exploitation of CVE-2023-22527 on an exposed Windows Confluence server. This led to the
Continue ReadingLightSpy Malware Now Targets Facebook & Instagram Data
Threat Overview The recent threat report published by AlienVault on February 21, 2025, highlights a significant evolution in the LightSpy malware framework. Initially designed to target mobile devices, LightSpy has now expanded its capabilities to compromise
Continue ReadingThe Bleeding Edge of Phishing: darcula-suite 3.0 Enables DIY Phishing of Any Brand | Netcraft
In the ever-evolving landscape of cyber threats, phishing remains one of the most pervasive and dangerous tactics employed by malicious actors. The recent threat report published by CyberHunter_NL on February 21, 2025, sheds light on a
Continue Reading