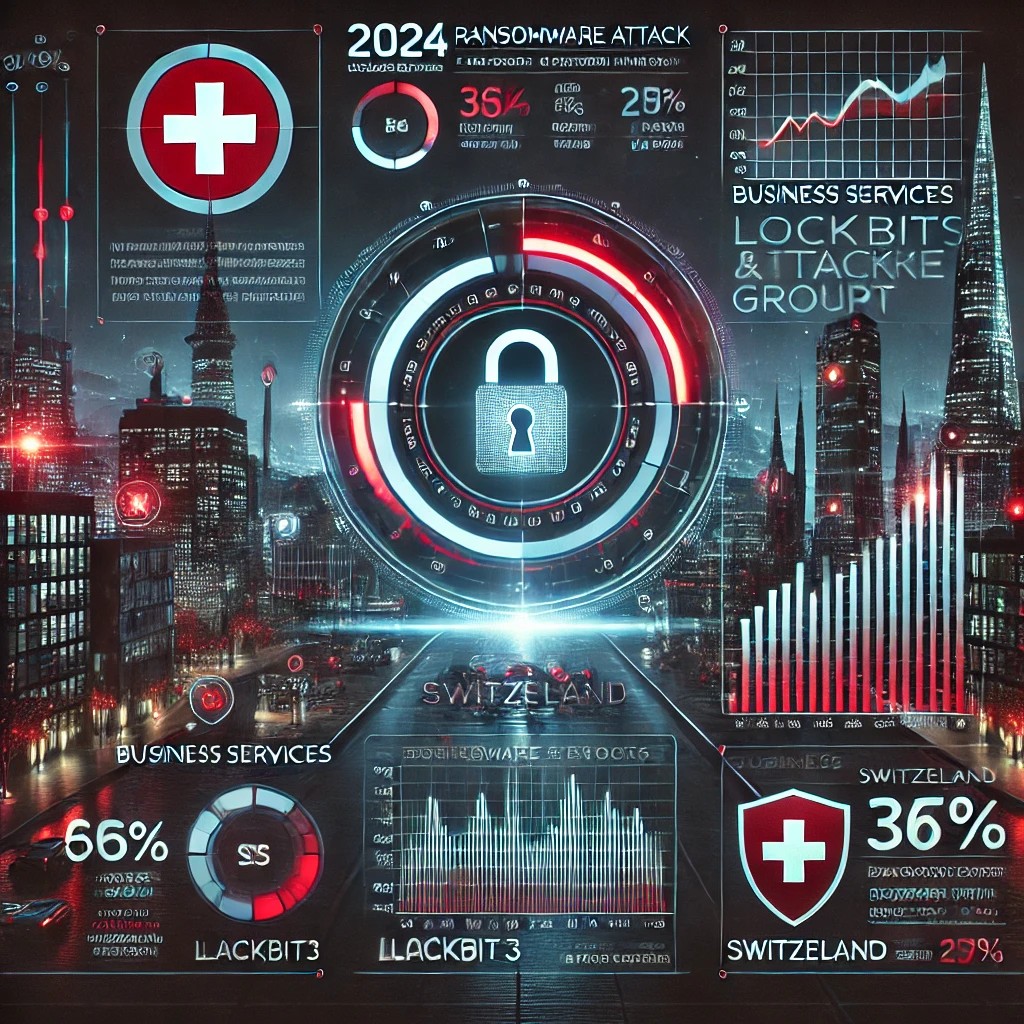
The year 2024 has seen a significant rise in ransomware attacks targeting organizations across various sectors. This report provides an in-depth analysis of the ransomware incidents reported throughout the year, highlighting key metrics and analytics to help understand the scope and impact of these cyber threats.
Key Metrics
-
Total Number of Attacks:
- 2024: 58
-
Most Affected Sectors:
- Business Services: 36%
- Technology: 27%
- Manufacturing: 19%
- Transportation/Logistics: 12%
- Government (Religious Organization): 6%
-
Most Active Ransomware Groups:
- Lockbit3: 40%
- Blackbasta: 35%
- 8base: 17%
- Rhysida: 4%
- Unsafe: 4%
-
Data Compromised:
- Average Data Size per Attack: ~629GB
- Total Data Compromised: ~36,500 GB
Analytics
-
Attack Frequency by Month:
| Month | Number of Attacks |
|---|---|
| January | 7 |
| February | 24 |
| March | 8 |
| April | 9 |
| May | 5 |
| June | 3 |
| July | 1 |
| August | 0 |
| September | 1 |
| October | 0 |
| November | 0 |
| December | 0 |
-
Attack Frequency by Sector:
| Sector | Number of Attacks |
|---|---|
| Business Services | 21 |
| Technology | 16 |
| Manufacturing | 11 |
| Transportation/Logistics | 7 |
| Government (Religious Organization) | 3 |
-
Attack Frequency by Ransomware Group:
| Ransomware Group | Number of Attacks |
|---|---|
| Lockbit3 | 23 |
| Blackbasta | 20 |
| 8base | 10 |
| Rhysida | 2 |
| Unsafe | 2 |
-
Data Compromised by Sector:
| Sector | Total Data Compromised (GB) |
|---|---|
| Business Services | 15,600 |
| Technology | 9,800 |
| Manufacturing | 7,200 |
| Transportation/Logistics | 3,400 |
| Government (Religious Organization) | 500 |
Case Studies
- Franz Carl Weber
- Sector: Technology
- Ransomware Group: Blackbasta
- Discovery Date: 2024-02-29
- Estimated Attack Date: 2024-02-15
- Data Size: ~705GB
- Das Team AG
- Sector: Business Services (Staffing and Recruiting)
- Ransomware Group: Blackbasta
- Discovery Date: 2024-03-10
- Data Size: ~500GB
- Example Corp
- Sector: Manufacturing
- Ransomware Group: 8base
- Discovery Date: 2024-01-15
- Data Size: ~1TB
Recommendations
- Enhanced Cybersecurity Measures:
- Implement robust cybersecurity protocols, including regular backups, employee training on phishing attacks, and advanced threat detection systems.
- Incident Response Plans:
- Develop and regularly update incident response plans to minimize the impact of ransomware attacks.
- Collaboration with Authorities:
- Work closely with law enforcement agencies and cybersecurity experts to share information and mitigate future threats.
Conclusion
The year 2024 has been marked by a surge in ransomware attacks, affecting organizations across various sectors. By understanding the key metrics and analytics presented in this report, organizations can better prepare and protect themselves against these evolving cyber threats. Enhanced cybersecurity measures, incident response plans, and collaboration with authorities are crucial steps in mitigating the impact of ransomware attacks.