Threat Overview
A recent threat report published by AlienVault on October 28, 2025, sheds light on sophisticated cyber campaigns orchestrated by the BlueNoroff threat group. Known for their financially motivated attacks, BlueNoroff has expanded its tactics to include comprehensive data acquisition and supply chain attacks.
Threat Actor Group: BlueNoroff
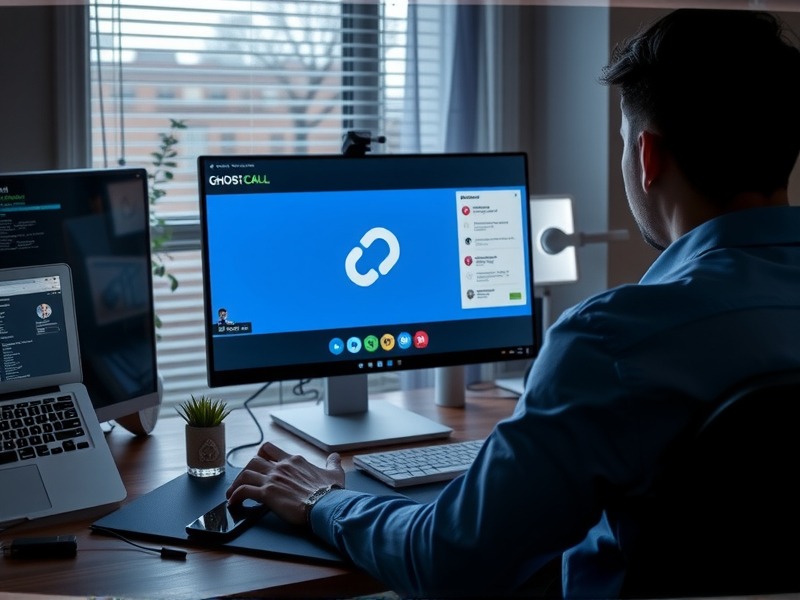
The BlueNoroff threat actor group is notorious for conducting highly sophisticated cyber operations aimed at financial gain. Their latest campaigns, dubbed GhostCall and GhostHire, demonstrate a significant evolution in their attack strategies. These campaigns target macOS devices of tech executives and venture capitalists through fake Zoom-like meetings, as well as Web3 developers through fraudulent recruitment processes.
Campaign Details
The GhostCall campaign focuses on tricking tech executives and venture capitalists into joining what appears to be legitimate Zoom meetings. These meetings are actually malicious, designed to deploy various malware strains onto the target’s macOS devices. The GhostHire campaign, on the other hand, targets Web3 developers by luring them with fake job offers. Once engaged, the developers are subjected to a series of social engineering tactics that lead to the deployment of sophisticated malware.
Malware Chains and Techniques
The campaigns utilize an array of malware chains, including ZoomClutch, DownTroy, CosmicDoor, RooTroy, and SilentSiphon. These malware strains are deployed across multiple operating systems, including Windows, macOS, and Linux, showcasing the group’s versatility and technical prowess.
The attacks involve several stages:
- Social Engineering: Initial contact is made through fake meetings or job offers to build trust with the target.
- AI-Enhanced Images: Advanced AI techniques are used to create convincing visuals that mimic legitimate communications.
- Multi-Stage Malware Deployment: The malware is deployed in stages, ensuring a deeper infiltration into the target’s system and network.
Impact and Objectives
BlueNoroff’s campaigns are not limited to cryptocurrency theft. Their objectives have expanded to include comprehensive data acquisition, enabling supply chain attacks and leveraging established trust relationships for broader impact. This shift indicates a more strategic approach aimed at long-term infiltration and control.
Recommendations
To mitigate the risks posed by BlueNoroff’s campaigns, security analysts and organizations should consider the following recommendations:
- Enhanced User Training: Educate employees about social engineering tactics and the importance of verifying the authenticity of communications, especially those involving meetings or job offers.
- Advanced Threat Detection: Implement advanced threat detection mechanisms that can identify and block multi-stage malware deployments across different operating systems.
- Regular Security Audits: Conduct regular security audits to identify vulnerabilities in the supply chain and ensure robust protection against potential infiltration.
- AI-Driven Security Solutions: Utilize AI-driven security solutions that can detect and mitigate threats enhanced by artificial intelligence techniques.
- Network Segmentation: Implement network segmentation to limit the spread of malware within the organization’s infrastructure.
- Incident Response Planning: Develop and regularly update incident response plans to quickly address and contain any detected threats.
External References
For additional information, please refer to the following external references: