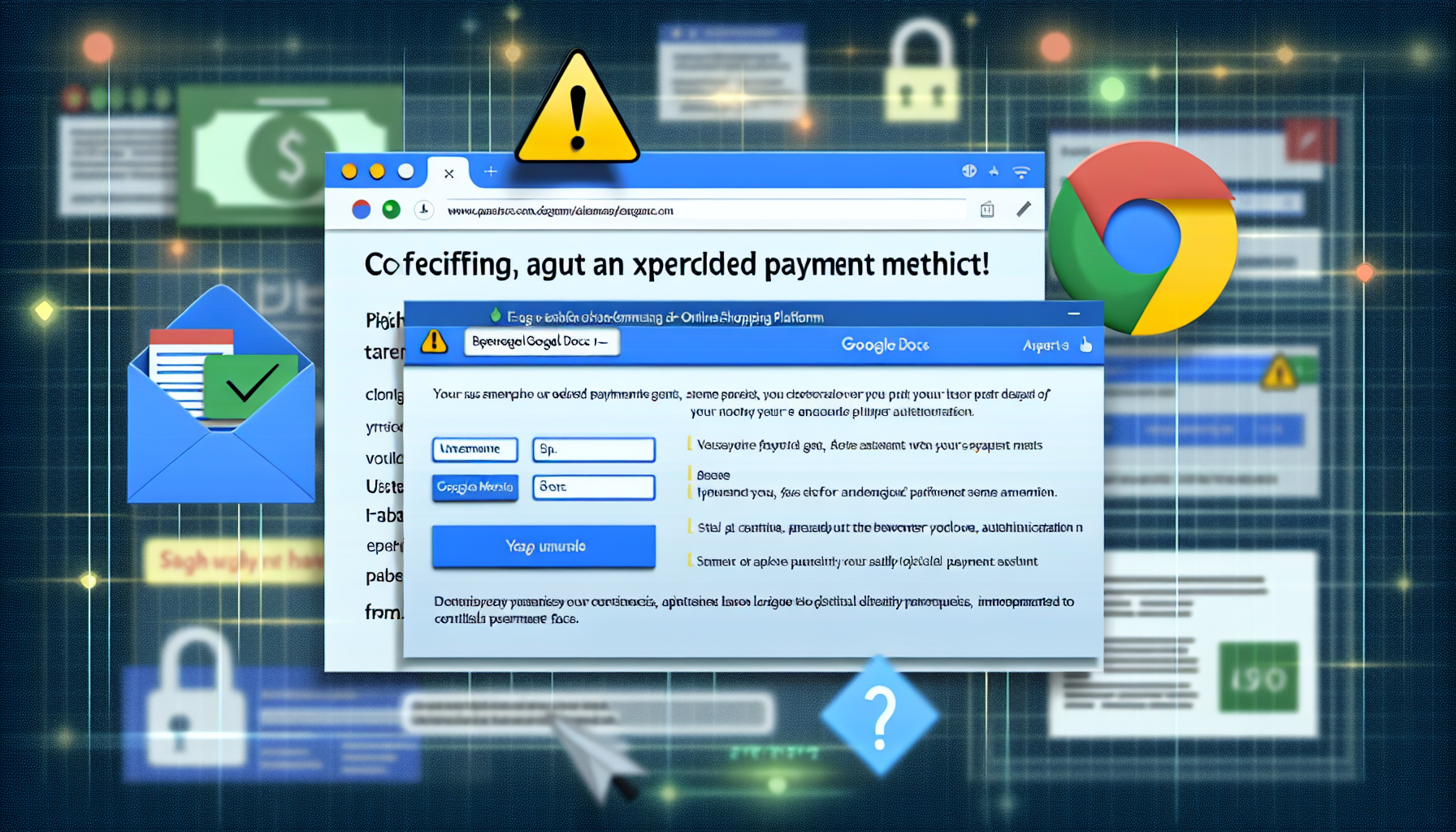
In the ever-evolving landscape of cyber threats, a new phishing scheme targeting Amazon Prime users has been identified. This sophisticated campaign aims to steal login credentials, verification information, and payment data, making it a significant concern for both individual users and the broader technology sector.
The threat report, published by AlienVault on February 18, 2025, provides a detailed analysis of this phishing scheme. The attack begins with a spoofed email that claims the user’s payment method has expired. This initial contact is designed to create a sense of urgency, prompting users to take immediate action. Clicking the update button in the email redirects victims to a fake Amazon security alert hosted on Google Docs. From there, they are led to a fraudulent login page where personal details, address information, and payment card data are requested.
This phishing campaign is particularly dangerous due to its resemblance to legitimate Amazon processes. The use of familiar branding and the mimicry of standard security procedures make it difficult for unsuspecting users to distinguish between genuine communications and malicious attempts. The sophistication of this scheme underscores the need for heightened vigilance and robust cybersecurity measures.
The report highlights several key tactics, techniques, and procedures (TTPs) employed by the threat actors. These include social engineering through spoofed emails, the use of legitimate-looking documents hosted on trusted platforms like Google Docs, and the creation of convincing fake login pages. The ultimate goal is to bypass security measures and gain unauthorized access to sensitive information.
To mitigate the risks associated with this phishing campaign, users are advised to follow several best practices:
- Verify Sender Authenticity: Always check the email address of the sender to ensure it matches the official domain of the company. Phishing emails often use slight variations or misspellings to deceive recipients.
- Direct Login: Instead of clicking on links in emails, log in directly to your Amazon account by typing the URL into your browser. This ensures that you are accessing the legitimate website and not a fake one.
- Contact Customer Service: For any inquiries or concerns about your account, contact customer service directly through official channels. Avoid using contact information provided in suspicious emails.
- Enable Two-Factor Authentication (2FA): Adding an extra layer of security can help protect your account even if your credentials are compromised. 2FA requires a second form of verification, such as a code sent to your mobile device.
- Educate Yourself: Stay informed about the latest phishing techniques and common tactics used by cybercriminals. Regular training and awareness programs can help you recognize and avoid potential threats.
The technology sector, which includes private entities related to research, development, manufacturing, and distribution of electronics, software, computers, and information technology products, is particularly vulnerable to such attacks. The interconnected nature of modern technologies means that a breach in one area can have far-reaching consequences. Therefore, it is crucial for organizations within this sector to implement comprehensive cybersecurity strategies.
The report by AlienVault provides valuable insights into the TTPs used in this phishing campaign and offers recommendations for mitigation. By understanding these tactics, users and organizations can better protect themselves against similar threats in the future. The confidence level of 100% and the reliability rating of A indicate that this report is completely trustworthy.
For additional information, you can refer to the external references provided in the report:
- https://securityboulevard.com/2025/02/amazon-phish-hunts-for-security-answers-and-payment-information/
- https://otx.alienvault.com/pulse/67b50f0432f066c6add22ef3
In conclusion, the Amazon Phish Hunts for Security Answers and Payment Information report serves as a critical reminder of the ongoing threat posed by phishing attacks. By staying vigilant, educating ourselves, and implementing robust security measures, we can better protect our personal information and safeguard against these malicious schemes.
Discover more from ESSGroup
Subscribe to get the latest posts sent to your email.