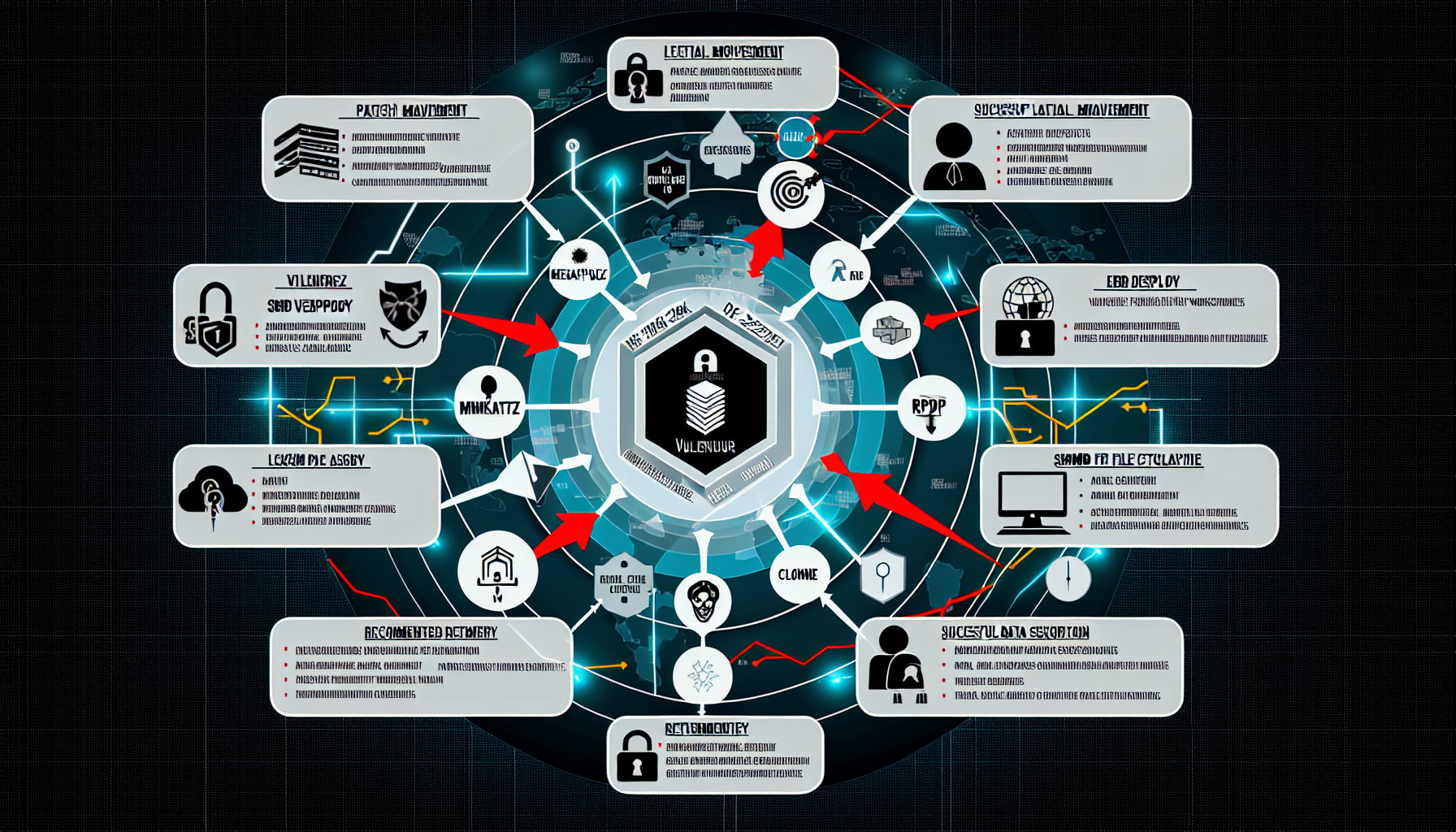
Threat Report: Confluence Exploit Leads to LockBit Ransomware\n\nOn February 24, 2025, AlienVault published a threat report detailing an intrusion that began with the exploitation of CVE-2023-22527 on an exposed Windows Confluence server. This led to the deployment of LockBit ransomware across the environment. The threat actor, whose identity is yet to be confirmed, exhibited advanced tactics and utilized various tools including Mimikatz, Metasploit, and AnyDesk.\n\nAttack Overview\n- The intrusion started with a successful exploit of CVE-2023-22527 on an exposed Confluence server.
– The threat actor leveraged RDP for lateral movement within the network.
– They deployed ransomware through multiple methods, including SMB file copying and automated distribution via PDQ Deploy.
– Sensitive data was exfiltrated using Rclone to MEGA.io cloud storage.
– The intrusion had a rapid Time to Ransom of approximately two hours, demonstrating the efficiency of the attack.\n\nRecommended Actions\n1. Patch Management: Ensure all systems are up-to-date with the latest security patches. In this case, applying the patch for CVE-2023-22527 would have prevented the initial intrusion.
2. Network Segmentation: Implement strict network segmentation to contain potential threats and limit lateral movement.
3. Access Control: Enforce the principle of least privilege (PoLP) to minimize the impact of compromised credentials.
4. Endpoint Detection and Response (EDR): Deploy EDR solutions to detect and respond to advanced threats in real-time.
5. Regular Backups: Maintain regular, secure backups to facilitate rapid recovery in case of a ransomware attack.\n\nExternal References\n- The DFIR Report
– AlienVault OTX\n\nExcerpt\nA threat report by AlienVault details an advanced intrusion starting with the exploitation of CVE-2023-22527, leading to LockBit ransomware deployment and data exfiltration. Organizations are advised to patch systems promptly, segment networks, enforce access control, deploy EDR solutions, and maintain regular backups.\n\nStatus: published
Discover more from ESSGroup
Subscribe to get the latest posts sent to your email.