Threat Report Overview
The cybersecurity landscape continues to evolve, with threat actors constantly developing new tactics, techniques, and procedures (TTPs) to evade detection and maximize their impact. In June 2025, a significant threat report was published by AlienVault, detailing a fileless AsyncRAT campaign targeting German-speaking users. This report underscores the sophistication of modern cyber threats and the need for robust security measures.
Threat Details
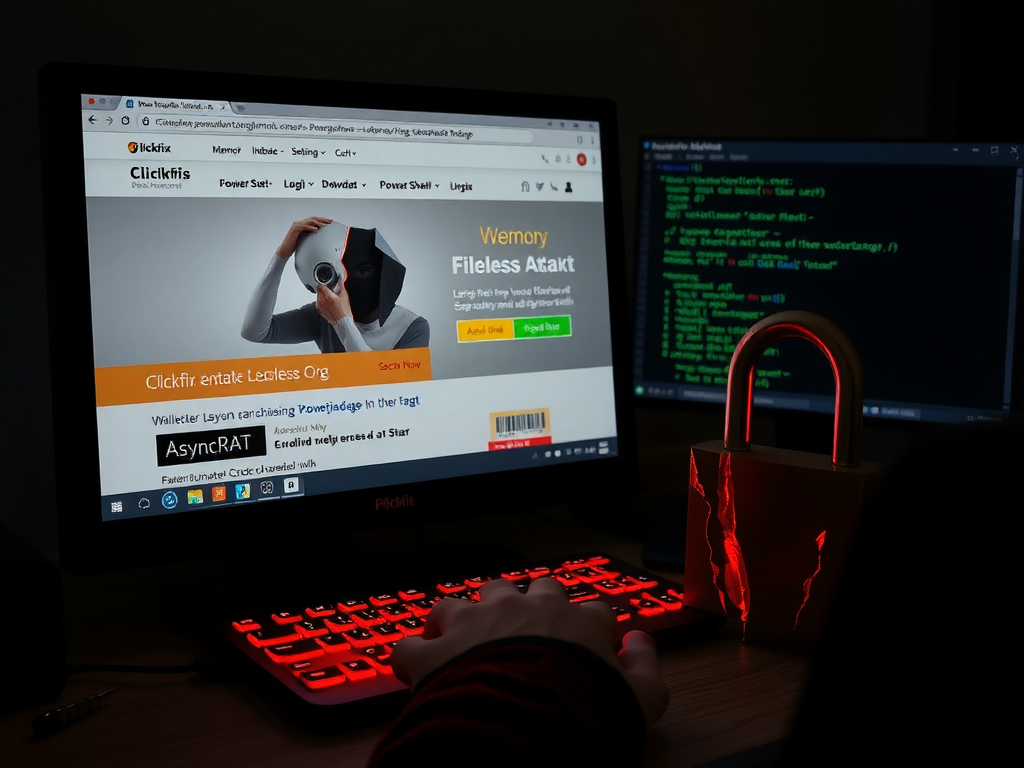
The report, titled ‘Fileless AsyncRAT Distributed Via Clickfix Technique Targeting German Speaking Users,’ provides an in-depth analysis of a malicious campaign that has been active since at least April 2025. The threat leverages a fileless attack method to distribute the AsyncRAT malware through Clickfix-themed websites, primarily affecting users in German-speaking regions.
The attackers use a fake ‘I’m not a robot’ prompt to trick users into executing malicious PowerShell code. This code downloads and runs obfuscated C# code directly in memory, allowing the malware to evade traditional disk-based detection methods. The fileless nature of this attack makes it particularly challenging to detect and mitigate.
Once executed, the AsyncRAT malware establishes full remote access to the compromised system, enabling credential theft and data exfiltration without leaving traces on the disk. This level of stealth is a significant concern for organizations and individuals alike.
Technical Analysis
The threat report reveals several key technical aspects of this campaign:
- Obfuscation Techniques: The attackers use advanced obfuscation techniques to conceal the malicious C# code, making it difficult for security tools to identify and block the threat.
- In-Memory Execution: By running the malware in memory, the attackers avoid leaving artifacts on the disk that could be detected by traditional antivirus software.
- Registry Persistence: The malware establishes persistence through registry keys, ensuring it remains active even after system reboots.
- Command and Control (C&C) Communication: The malware communicates with a C&C server on port 4444, allowing the attackers to issue commands and exfiltrate data.
Mitigation Strategies
To protect against this fileless AsyncRAT campaign, several mitigation strategies are recommended:
- Block Suspicious PowerShell Activity: Implementing strict controls on PowerShell activity can help prevent the execution of malicious scripts. Organizations should monitor for unusual PowerShell commands and restrict their use where possible.
- Monitor Registry Changes: Regularly monitoring registry changes can help detect unauthorized modifications that may indicate malware persistence.
- In-Memory Scanning: Deploying in-memory scanning solutions can identify and mitigate threats that operate solely in memory, providing an additional layer of defense against fileless attacks.
- User Education: Educating users about the risks associated with interacting with suspicious websites and prompts can significantly reduce the likelihood of successful phishing attempts.
Recommendations for Security Operation Centers
Security operation centers (SOCs) play a crucial role in detecting and responding to sophisticated cyber threats. To effectively counter this fileless AsyncRAT campaign, SOC teams should:
- Enhance Detection Capabilities: Investing in advanced threat detection tools that can identify obfuscated code and in-memory execution is essential for staying ahead of these attacks.
- Implement Behavioral Analytics: Using behavioral analytics to detect anomalies in user and system behavior can help identify potential threats before they cause significant damage.
- Regularly Update Security Protocols: Keeping security protocols up-to-date with the latest threat intelligence ensures that SOCs are prepared to respond to emerging threats effectively.
Conclusion
The fileless AsyncRAT campaign targeting German-speaking users highlights the evolving nature of cyber threats and the need for robust, multi-layered security measures. By understanding the TTPs used in this campaign and implementing recommended mitigation strategies, organizations can significantly enhance their defenses against such sophisticated attacks. Continuous vigilance, user education, and investment in advanced detection technologies are key to maintaining a secure digital environment.
For more detailed information on this threat report and additional recommendations, please refer to the external references provided below:
- https://www.cloudsek.com/blog/fileless-asyncrat-distributed-via-clickfix-technique-targeting-german-speaking-users
- https://otx.alienvault.com/pulse/6850162664e0f589c91291f6
By staying informed and proactive, organizations can better protect themselves against the ever-changing landscape of cyber threats.
Discover more from ESSGroup
Subscribe to get the latest posts sent to your email.