Discover more from ESSGroup
Subscribe to get the latest posts sent to your email.
Threat Overview
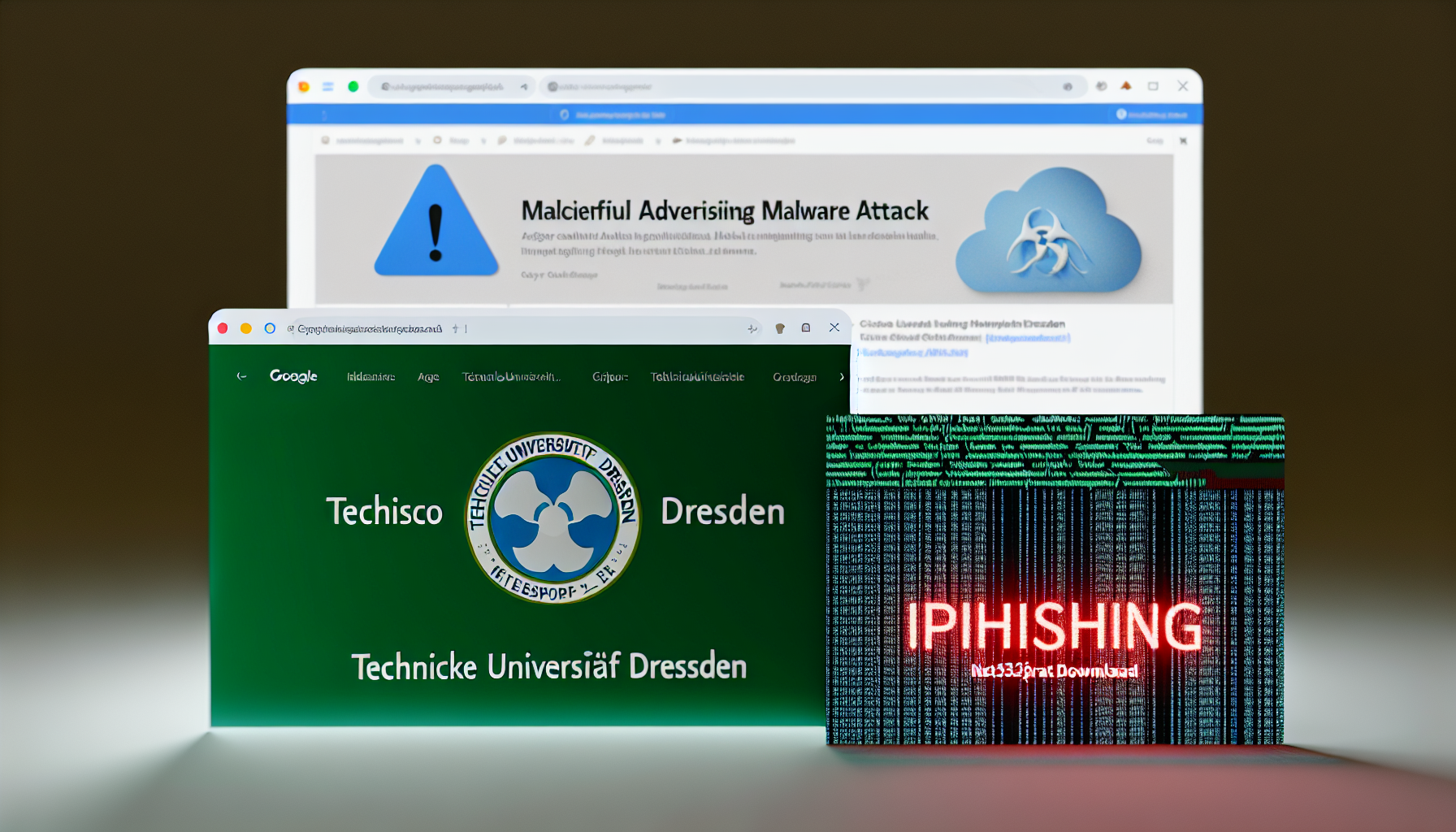
sophisticated cybercrime operation involving malicious advertising (malvertising) has been discovered by Malwarebytes and CyberHunter_NL. The threat actors are exploiting users searching for ‘cisco anyconnect’ by displaying a convincing Google ad with a deceptive URL, mimicking a legitimate Cisco domain.
Attack Vector
– Malicious Ad: The attack begins with a malicious Google ad that appears when users search for ‘cisco anyconnect’.
– Decoy Website: Attackers used content from the website of Technische Universität Dresden (TU Dresden) to create a convincing decoy site.
– Server-Side Checks: Upon clicking the ad, server-side checks determine if the user is a potential victim based on their IP address and network settings.
– Malware Payload: Real victims are redirected to a phishing site for Cisco AnyConnect, where they download a malicious installer (client32.exe) associated with the NetSupport RAT.
Indicators of Compromise
– Malvertising Infrastructure: anyconnect-secure-client[.]com, cisco-secure-client[.]com[.]vissnatech[.]com
– NetSupport RAT Download: berrynaturecare[.]com/wp-admin/images/cisco-secure-client-win-5[.]0[.]05040-core-vpn-predeploy-k9[.]exe (MD5 Hash: 78e1e350aa5525669f85e6972150b679d489a3787b6522f278ab40ea978dd65d)
– NetSupport RAT Command and Control (C2) Servers: monagpt[.]com, mtsalesfunnel[.]com
– IP Addresses: 91.222.173[.]67/fakeurl.htm and 199.188.200[.]195/fakeurl.htm
Recommendations
– Be cautious when downloading programs, especially from sponsored search results.
– Keep systems and software up-to-date with the latest security patches.
– Use reliable antivirus solutions and maintain robust security protocols.
Source(s)
Subscribe to get the latest posts sent to your email.
Lorem Ipsum is simply dummy text of the printing and typesetting
industry. Lorem Ipsum has been the industry's
Threat Overview
The upcoming German federal elections on February 23, 2025 are under significant threat from Russian influence operations. According to a recent report published by AlienVault on February 13, 2025, these operations aim to disrupt the democratic process and sway public opinion in favor of pro-Russian sentiments. The report highlights several key campaigns, including Doppelgänger, Operation Overload, CopyCop, Operation Undercut, and the Russia-based Foundation to Battle Injustice.
These influence operations are designed to exacerbate German sociopolitical divisions by spreading manipulated content and fostering anti-US and EU sentiment. The ultimate goal is to undermine NATO unity and create a more fragmented political landscape in Germany. While these efforts have not yet significantly altered voter behavior or public opinion as of mid-February, the persistent nature of these campaigns poses an ongoing risk to media integrity and public trust.
The tactics employed by these operations are evolving rapidly. They include expanding to new platforms like Bluesky, launching new brands and websites, and utilizing AI-based tools to enhance their reach and effectiveness. The use of AI in particular is a concerning development, as it allows for more sophisticated and targeted manipulation of information.
One of the most alarming aspects of these operations is their ability to adapt and evolve. For instance, Doppelgänger involves creating fake social media accounts that mimic legitimate sources to spread disinformation. Operation Overload focuses on overwhelming social media platforms with pro-Russian content to drown out opposing viewpoints. CopyCop involves copying and reposting content from credible sources but altering it slightly to fit a pro-Russian narrative.
Operation Undercut, on the other hand, targets specific individuals or groups within German society who are influential in shaping public opinion. The Foundation to Battle Injustice is a more overtly political operation that aims to present Russia as a champion of justice and democracy, contrasting it with what they portray as the oppressive regimes of the US and EU.
The report by AlienVault underscores the importance of vigilance and preparedness in the face of these threats. It highlights the need for robust cybersecurity measures, media literacy programs, and international cooperation to counter these influence operations effectively. The report also emphasizes the role of social media platforms in mitigating the spread of disinformation.
Recommendations
Conclusion
The threat posed by Russian influence operations targeting the German elections is real and evolving. While these efforts have not yet significantly impacted voter behavior or public opinion, their persistence and adaptability require constant vigilance. By implementing robust cybersecurity measures, promoting media literacy, fostering international cooperation, ensuring transparency on social media platforms, and launching public awareness campaigns, we can mitigate the risks posed by these influence operations.
For additional information, please refer to the full report published by AlienVault: https://go.recordedfuture.com/hubfs/reports/ta-ru-2025-0213.pdf. This comprehensive document provides detailed insights into the tactics, techniques, and procedures (TTPs) used in these operations, as well as recommendations for mitigation.
The reliability of this report is rated A – Completely reliable, with a confidence level of 100%. The report contains 34 connected elements and includes external references for further reading: https://otx.alienvault.com/pulse/67adcbf1207c33eff5891ca2.
In conclusion, the upcoming German elections are at a critical juncture. The threat of Russian influence operations is significant, but with the right measures in place, we can safeguard the integrity of the democratic process and protect public trust.

Threat Overview
A recent threat report published by AlienVault, titled “Examining Redtail: Analyzing a Sophisticated Cryptomining Malware and its Advanced Tactics”, highlights the growing sophistication of cryptocurrency mining malware. The report analyzes Redtail, a stealthy cryptominer that employs advanced techniques to avoid detection.
Redtail – Key Features
The report unveils several notable features of Redtail:
* Stealthy installation and evasion tactics
* Utilizes additional scripts to identify CPU architecture and remove existing miners
* Originates from IP addresses in the Netherlands and Bulgaria
* Exploits weak root login credentials for initial compromise
* Employs SFTP for transferring malicious files
Protection Strategies
Based on the analysis, AlienVault recommends the following strategies to protect against Redtail and similar threats:
* Regular patching to address known vulnerabilities
* Deploy robust antimalware solutions to detect and block Redtail
* Disable direct root logins to prevent unauthorized access
* Implement SSH shared keys or TCP Wrappers for better control over network traffic
* Use Security Information and Event Management (SIEM) systems for centralized log monitoring
The Evolving Threat of Cryptomining Malware
The report underscores the continuous evolution of cryptocurrency mining malware. The sophistication displayed by Redtail serves as a reminder that comprehensive cybersecurity measures and ongoing vigilance are crucial in protecting against advanced threats.
Resources
For more information on this threat:
* SANS Internet Storm Center Daily Diary: https://isc.sans.edu/diary/rss/31568


As cyber threats evolve, ensuring robust system security has become more critical than ever. Whether you’re managing personal data or running a nonprofit organization, taking proactive steps to secure your systems is essential. Here are five easy steps to enhance your system security in 2024
By following these steps, you can significantly enhance your system security in 2024.

Subscribe now to keep reading and get access to the full archive.