Threat Overview
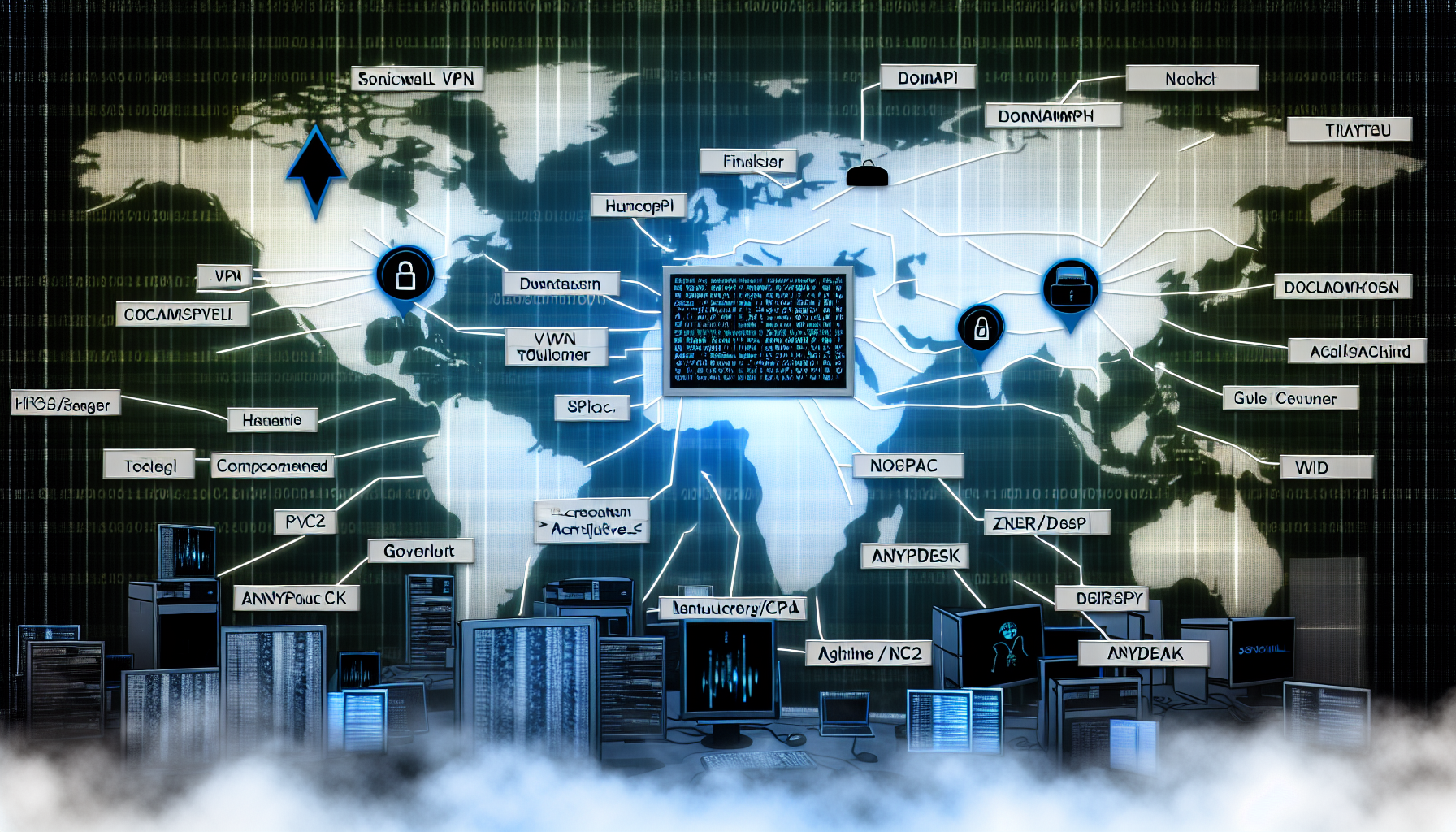
The Security Operations Center (SOC) has identified a significant threat report published by AlienVault on April 28, 2025. Titled Navigating Through The Fog, this report details an alarming discovery of an open directory linked to a Fog ransomware affiliate. This directory contained a variety of tools designed for reconnaissance, exploitation, lateral movement, and persistence within targeted networks.
Initial Access
The initial access vector involved compromised SonicWall VPN credentials. This method highlights the importance of securing remote access points, as they often serve as entry points for cyber threats. The use of compromised credentials underscores the need for robust authentication mechanisms and continuous monitoring of access logs to detect anomalous activities.
Reconnaissance and Exploitation Tools
The toolkit discovered in the open directory included several sophisticated tools:
- SonicWall Scanner: Used for identifying vulnerabilities within SonicWall devices.
- DonPAPI: A tool designed for credential theft from Windows systems.
- Certipy: Utilized for exploiting Active Directory Certificate Services (AD CS).
- Zer0dump: Employed for dumping credentials from memory.
- Pachine/noPac: Tools for bypassing Kerberos Constrained Delegation.
These tools were used to perform extensive reconnaissance and exploitation, allowing the threat actors to gain a deep understanding of the targeted networks and identify critical vulnerabilities.
Lateral Movement
Once initial access was established, the threat actors employed various techniques for lateral movement. This included exploiting Active Directory vulnerabilities and using credential theft tools like DonPAPI and Zer0dump. The use of these tools enabled the attackers to move laterally within the network, compromising additional systems and escalating their privileges.
Persistence Mechanisms
To maintain persistence within the compromised networks, the threat actors utilized AnyDesk, a remote desktop software. This was automated through a PowerShell script, ensuring that the attackers could regain access even if their initial entry points were discovered and mitigated. The use of legitimate tools like AnyDesk makes detection more challenging, as they are commonly used in legitimate operations.
Command-and-Control Operations
The report also revealed the use of Sliver C2 executables for command-and-control (C2) operations. These executables allowed the threat actors to communicate with and control compromised systems remotely. The use of sophisticated C2 frameworks indicates a high level of sophistication and resources available to the attackers.
Victimology
The victims spanned multiple industries across Europe, North America, and South America. This broad targeting scope highlights the global reach and impact of the Fog ransomware affiliate. Industries affected included finance, healthcare, manufacturing, and government sectors, among others. The diverse range of targets suggests that the threat actors are opportunistic and willing to exploit any vulnerabilities they encounter.
Recommendations for Mitigation
In light of this threat report, the SOC recommends the following measures to enhance cybersecurity posture:
- Strengthen Remote Access Security: Implement multi-factor authentication (MFA) for all remote access points, including VPNs. Regularly review and update access logs to detect any suspicious activities.
- Patch Management: Ensure that all systems and software are up-to-date with the latest security patches. Prioritize patching known vulnerabilities in critical infrastructure components like SonicWall devices.
- Credential Hygiene: Enforce strong password policies and regularly rotate credentials. Use tools like DonPAPI to monitor for credential theft attempts within the network.
- Active Directory Security: Implement best practices for securing Active Directory, including disabling unnecessary services and monitoring for suspicious activities related to AD CS.
- Network Segmentation: Segment the network to limit lateral movement. Use firewalls and access controls to restrict communication between different segments of the network.
- Endpoint Protection: Deploy advanced endpoint protection solutions that can detect and block sophisticated threats like Sliver C2 executables.
- Incident Response Planning: Develop and regularly update incident response plans to quickly detect, respond to, and mitigate cyber threats. Conduct regular tabletop exercises to ensure readiness.
By implementing these recommendations, organizations can significantly enhance their cybersecurity posture and reduce the risk of falling victim to sophisticated cyber threats like those detailed in the Navigating Through The Fog report.
For additional information, please refer to the following external references:
- https://thedfirreport.com/2025/04/28/navigating-through-the-fog
- https://otx.alienvault.com/pulse/680f0738479d23f04a10d198
Please check the following page for additional information: https://thedfirreport.com/2025/04/28/navigating-through-the-fog
Discover more from ESSGroup
Subscribe to get the latest posts sent to your email.